SSH Secure Collaboration 2024

NEW SSH SECURE COLLABORATION 2024
IS HERE!
SECURE CHAT, SECURE ROOM, SECURE MAIL
Encrypted video conferencing, files and file sharing, calls and messages. We secure all your critical communications.

Your channels for sharing confidential, restricted, or secret information
Secure Collaboration 2024 makes encrypting emails, chats, workspaces, and audio/video communications
for privacy, compliance, and record-keeping easy.
All-in-one solution. Includes Secure Messaging 2024
and Secure Mail 2024.
Your channels for sharing confidential, restricted, or secret information
Secure Collaboration 2024 makes it easy to encrypt emails, messages, chat rooms, and audio/video communications for privacy, compliance, and record-keeping. All-in-one solution. Includes Secure Messaging 2024 and Secure Mail 2024.
Avoid non-compliance and large regulatory fines with authorized channels for your sensitive communications
The Securities and Exchange Commission (SEC) fined Wall Street companies for pervasive and longstanding off-channel business communications over platforms like iMessage, WhatsApp, and Signal. The fines exceeded $4 billion.
Affected businesses include Bank of America, Citigroup, and Goldman Sachs Group.
Build authorized channels for your sensitive communications
Borderless communications
Enable super secure live communications and message sending across organizations. Allow verified-only external stakeholders to send confidential messages to you conveniently from a web browser.
Your data under your control
Meet data sovereignty requirements with public cloud, private cloud, or on-premises deployments. Send messages without leaving a trace on public servers. Control your own encryption keys.
Up to 1GB of data
Regular email or chat services allow sending attachments with up to 30MB of data. With our solution, the limit is 1GB.
Verify sender and recipient
Choose from various authentication methods, including MFA, OTP, PIN, SSO, and bank IDs. Flexible permissions control.
Record-keeping done right
Solid audit trail and evidence of sending and receiving communications to pass audits and compliance requirements with flying colors.
Always-on security
For us, security is not an option, it's the default setting. Your data is always protected by robust end-to-end encryption (AES-256, Olm and Megolm).
Trusted provider
Our solutions (Secure Mail and NQX) are approved by the National Cyber Security Centre Finland (NCSC-FI) for TL III (EU CONFIDENTIAL) and TL IV (EU RESTRICTED) levels for national classified information.
Customers in highly regulated industries
Among our customers are private as well as public institutions, including governments and governmental agencies.
Cybersecurity expertise
We have more than 20 years of experience in developing and building cybersecurity solutions that ensure security now and in the future.
What our customers say about SSH Secure Collaboration 2024
We think that encrypting and protecting critical information sharing needs to be easy. And our customers agree.
Secure Email is surprisingly easy to use. Just add ”.s” to the end of the recipient and the message is encrypted.
- Head of HR, Financial institution
For years, we have been using SSH's solution to protect email and e-communications. The solution meets our requirements for data security and data protection very well, and above all, the solution is easy to use for both the sender and the recipient. One of the key criteria has been that the solution does not require any separate program installations from the recipient.
Partner, lawyer
NEW!
SSH Secure Collaboration 2024 includes:
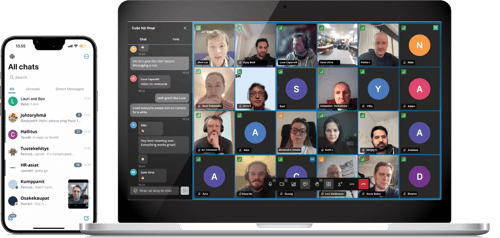
Secure Messaging 2024
Secure instant communications that allow you to build your own authorized channels and communicate in real time over encrypted messaging, voice, and video.
You are in full control over your communications with robust end-to-end security, flexible deployment (in the cloud or on-premises), and comprehensive monitoring features (including full audit trails and compliance reporting).
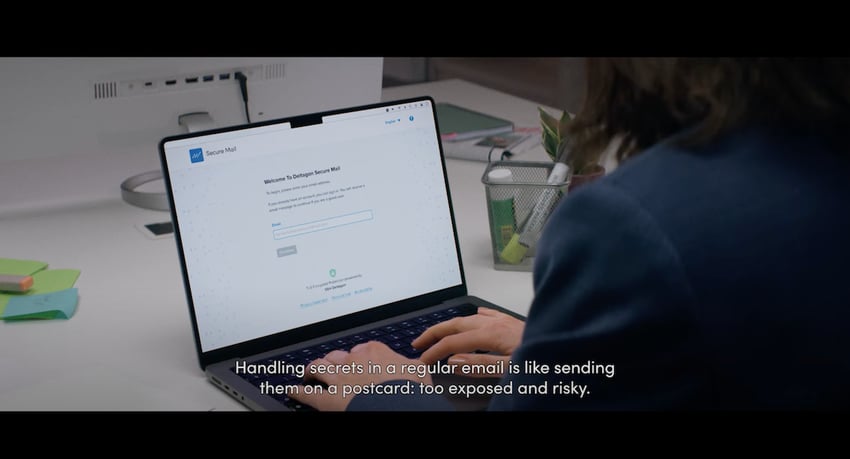
Secure Mail 2024
Easy-to-use and highly secure email encryption that works with all email providers (Gmail, Outlook, etc.) and requires no end-user accounts. Now with updated UI and functionality.
That means consistent UX across email services, low management overhead, and low maintenance and total costs.
Comes in various on-premise and cloud solutions with strong end-to-end encryption and strong authentication.
SSH Secure Business Communications Suite includes:
Secure Mail
Easy-to-use, secure email encryption that works with all email providers (Gmail, Outlook, etc.) and requires no end-user accounts.
That means consistent UX across email services, low management overhead, and low maintenance and total costs.
Comes in various on-premise and cloud solutions with strong end-to-end encryption and strong authentication.
Secure Rooms
Secure workspace with a responsive browser interface that works with any device and allows file sharing without limits.
Support for various authentication methods (MFA, SSO) allows secure two-way communication with third parties.
Strong encryption and simple admin tools ensure easy security controls.
Secure Forms
Data collection and form encryption made easy with a straightforward GUI and a wide variety of features for creating secure e-forms.
Developed to fulfill high-security needs with all data in transit protected with strong encryption.
Your confidential information stays under your control. You stay compliant with strict regulations, like GDPR or WCAG 2.1.
Secure Signatures
Secure digital signature solution protected by robust encryption that requires no end-user accounts for signatories to manage.
Support for your secure e-signature processes with flexible configuration (APIs or web interfaces), various authentication options, and flexible branding options.
On-premise deployment ensures your data stays under your control.
Learn more about secure business communications
Building your authorized and secure channels can be simple - with the right help. Check out some additional resources here.
GUIDE: The Essential Guide to Securing Critical Business Communications and Data Sharing
Get the guide
WHITE PAPER: Bolting a critical security layer onto Microsoft 365 for sensitive communications
Get the white paper
WHITE PAPER: Secure Business Communications as a Service - Why It Makes Sense for Managed Service Providers (MSPs)
Get the white paper
CASE STUDY: Secure Data Access and Data Protection in the Healthcare Industry
Read the case study
CASE STUDY: Sensitive Data Management - Digitalization and Automation of Business Funding Processes
Read the case study
DATASHEET: Secure Email Encryption
Get the datasheet
Book a demo of our suite to see it in action!